[SHOWTOGROUPS=4,20]
Summary
IP Radar 2, as the name implies, shows on the world map all IP addresses your machine is talking to.
This geographical representation of hosts with different IPs gives the name to this tool, in analogy to a standard Radar used to detect airplanes.
The analogy continues if we consider e.g. that Radars are able to locate flying objects which have a "transponder". This is the usual case in commercial airplanes who identify themselves to "secondary" Radars.
But in case of military air-crafts or smuggling planes, no contact over transponders is possible as they may be turned off intentionally. Then, the secondary Radar is blind.
In those cases, a "primary" Radar is required which locates planes not willing to identify themselves by illuminating a large portion of space with an electromagnetic wave and receiving back the reflected waves from targets within that space.
In IP Radar 2 we resolve the geographical location of hosts and also send a ping request (ICMP echo request) to them to get their replies, being able to calculate round trip time and packet loss statistics.
Some people say that the lack of ping replies does not necessarily mean that the host is willing to hide from us. Some servers try to protect themselves from Denial of Service attacks and do not reply to ping requests, some hosts just won't bother redirecting ICMP requests behind the NAT gateway or a corporate network.
Nevertheless, in my opinion, it is always suspicious when a host does not reply to my pings.
The representation of an airplane on a radar console may show several attributes like height, usually in feet above sea level. Similarly, in IP Radar 2, we show several information like the number of bytes transmitted to a specific host. This is seen in the height of the marker.
The described techniques for intrusion detection and prevention are for sure not the "strongest" against malicious network activity, but they work well
(*), providing a good compromise between complexity, real-time behavior and robustness. Many aspects of the proposed idea can be improved in future.
(*) things that I have detected with this tool so far:
- encrypted connections to a Linux mirror in a university in Ecuador – which, of course, I blocked. Probably a malware tunneling stuff?
- permanent background activities from Amazon, Microsoft and Google. Some of them could be reduced by deactivating unnecessary windows services. But most of it remains a backpack you need to carry when you are a Windows user.
- drawing tool from Bulgaria without certificate. Which I did not download.
- annoying user profiling for advertising from companies located in Paris.
- connections to cheap hosting servers every time my WiFi reconnects.
All these points show clearly that my PC has software running which I don't need and is probably harmful. None of the anti-viruses that I used detected them up to now, but wherever they hide, they are no longer able to do any damage.
Here, we see that the Tool actually helped increasing the security of my PC and is a meaningful complement to antivirus and firewall software.
After a couple of weeks of detecting "bad” guys almost daily, now I can say that I am free. Since 2 months, I only see nice "green” hosts (my firewall has now 85 additional blocking rules!).
Why Do We Need Something Like IP Radar 2 ?
Providers of firewalls and antivirus software offer the main measures for network security. Unfortunately, despite all features provided by these tools, our PCs still suffer under massive vulnerability problems. Infections with all kinds of exploits make these tools look like a Swiss cheese.
By combining their capabilities with custom IDPS features, security can be notably improved.
Typical Capture Session / Use Case
So, I wake up early in the morning and while sipping a cup of coffee, and before starting to read the newspaper, I check the world-map on my browser to see if there is something new.
This usually takes only a few seconds. If I only see green bubbles and blue lines, I know for sure that I am safe.
But if I see some red markers and red lines, then I know there may be some trouble.
In that case, a short glance on the map lets me locate the possible intruder in a remote corner of the world where I usually see no activity.
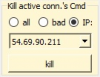
With one click on the corresponding IP address, I get more information displayed that shows that the owner is already on my black-list.
Oh no, a closer look shows that a connection with that IP is established at this very moment!
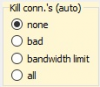
Damned! The option Kill connection was set to None.
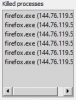
No problem, on request I kill now the process holding that connection.
That will solve the problem for now, but what about next time? Oh, now I see that a blocking rule for that IP has been automatically added to my firewall.
Everything is fine!
Now I can peacefully start my matutinal reading. ;-)
Using the Code
Besides this article and the links provided in it, I supply together with the code a short
READ_ME.txt file which shall help you with the initial steps.
Points of Interest
Borrowing some words from Andy Yen (see link above): "What we have here is just the first step, but it shows that with improving technology privacy doesn't have to be difficult, it doesn't have to be disruptive. Ultimately, privacy depends on each and everyone of us. And we have to protect it now because our online data is more than just a fractions of ones and zeros. It's actually a lot more than that. It's our lives, our personal stories, our friends, our families, and in some ways also our hopes and aspirations. So, now it's the time for us to stand up and say: yes, we do want to live in a world with online privacy. And yes, we can work together to turn this vision into reality!".
History
- 22nd May, 2020: Initial version
License
This article, along with any associated source code and files, is licensed under The Code Project Open License (CPOL)
[/SHOWTOGROUPS]