EurekaLog + VirusTotal = unforeseen consequences
We were contacted by a person who reported Для просмотра ссылки Войдиили Зарегистрируйся of uploading EurekaLog-enabled application to the Для просмотра ссылки Войди или Зарегистрируйся service.
It was like this: the client compiled an application with EurekaLog. The application was configured to send bug reports by e-mail. He uploaded the compiled application to the VirusTotal website, and got a scan result that everything is fine.
So far, everything is quite typical. The strange things started the next day, when the client received an e-mail with bug report from EurekaLog. The weird thing was that the client did not launch the application, and he did not distribute/deploy it. And the report itself looked... unusual.
In particular, the executable file was renamed to a random set of letters, as well as the username and computer name. There was nothing suspicious in the list of modules and processes, and in general the machine seemed "bare". The only aspect that stood out was the loaded pancore.dll, which has created one thread. Google suggests that pancore.dll is a part of Oracle AutoVue - an enterprise solution for visualizing and viewing CAD and similar data.
The answer to the "riddle" came later. This is what the results of analyzing the file looked like during the first check:
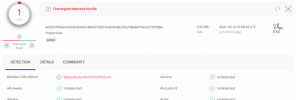
And here is what the site shows when re-uploading the same file a day later (after receiving the "mysterious" report):
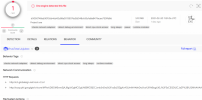
As you can see, the scan results have changed: "interesting" behavior patterns have been added to the title, and new tabs have appeared in the full report, containing the analysis of the file's behavior: which files it opens, which URLs it visits, which registry keys it changes, which processes it launches, and so on.
It turns out that VirusTotal runs uploaded apps in multiple virtual machines / sandboxes (aka multisandboxing) to determine details of its behavior. In particular, the file we uploaded has been verified in C2AE (presumably Для просмотра ссылки Войдиили Зарегистрируйся), Sysinternals Sysmon tool, and VirusTotal's own sandbox: Jujubox.
This feature has existed in VirusTotal since 2012, when Для просмотра ссылки Войдиили Зарегистрируйся - a clone of Для просмотра ссылки Войди или Зарегистрируйся. Для просмотра ссылки Войди или Зарегистрируйся in 2017, and Для просмотра ссылки Войди или Зарегистрируйся in 2019.
It is not hard to figure out that EurekaLog's report is a result of executing the uploaded file in one of these sandboxes (presumably - Jujubox). Now getting a "sudden" report does not seem so surprising anymore.
We were contacted by a person who reported Для просмотра ссылки Войди
It was like this: the client compiled an application with EurekaLog. The application was configured to send bug reports by e-mail. He uploaded the compiled application to the VirusTotal website, and got a scan result that everything is fine.
So far, everything is quite typical. The strange things started the next day, when the client received an e-mail with bug report from EurekaLog. The weird thing was that the client did not launch the application, and he did not distribute/deploy it. And the report itself looked... unusual.
In particular, the executable file was renamed to a random set of letters, as well as the username and computer name. There was nothing suspicious in the list of modules and processes, and in general the machine seemed "bare". The only aspect that stood out was the loaded pancore.dll, which has created one thread. Google suggests that pancore.dll is a part of Oracle AutoVue - an enterprise solution for visualizing and viewing CAD and similar data.
The answer to the "riddle" came later. This is what the results of analyzing the file looked like during the first check:

And here is what the site shows when re-uploading the same file a day later (after receiving the "mysterious" report):

As you can see, the scan results have changed: "interesting" behavior patterns have been added to the title, and new tabs have appeared in the full report, containing the analysis of the file's behavior: which files it opens, which URLs it visits, which registry keys it changes, which processes it launches, and so on.
It turns out that VirusTotal runs uploaded apps in multiple virtual machines / sandboxes (aka multisandboxing) to determine details of its behavior. In particular, the file we uploaded has been verified in C2AE (presumably Для просмотра ссылки Войди
This feature has existed in VirusTotal since 2012, when Для просмотра ссылки Войди
It is not hard to figure out that EurekaLog's report is a result of executing the uploaded file in one of these sandboxes (presumably - Jujubox). Now getting a "sudden" report does not seem so surprising anymore.
